By Brad Antoniewicz.
I've been an adjunct professor at NYU Poly for almost two years now. It's been a great experience for a number of reasons, one of which is because I'm teaching a hot topic: Vulnerability Analysis and Exploitation. The course is the next iteration of the pentest.cryptocity.net content that evolved into the CTF Field Guide by Dan Guido, Trail of Bits, and a bunch of other industry professionals. It takes a student with some minor programming knowledge and submerges them into exploitation. When the student comes out, they have successfully exploited IE on Windows 7, bypassing DEP and ASLR. It's an awesome, but sometimes overwhelming experience for every student who takes it.
Each semester I start the class off with a survey to gauge the student's experience level: No surprise here, most have little to no experience when it comes to real-world exploitation on Windows. This results in a "revamping" period for the student where they have to work extra hard getting used to WinDBG and IDA.
I wanted to create something that would help ease the students into the learning environment, and that's what FSExploitMe is; a tutorial that walks you through the basics of WinDBG and general exploitation in a browser environment.
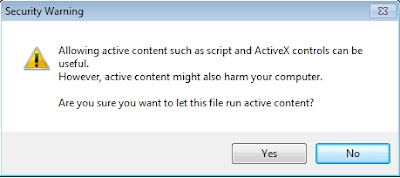
Next Internet Explorer will ask you if you'd like to allow the active content to run, click "Yes":
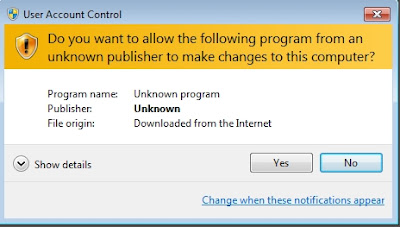
Then finally you'll get a UAC prompt, click "Yes" here as well:
FSExploitMe should be all ready to go now:
Internet Explorer 8 looks a little less pretty then newer versions. IE8 is the recommended version strictly because Lesson 3 of FSExploitMe executes a HeapSpray that will not work on newer versions of IE. You can easily replace that function to use a newer HeapSpray, I just haven't done that and tested it on all other IE versions. That being said, future iterations of FSExploitMe will include a more robust HeapSpray Function.
It will help to have Symbols when you start debugging. The easiest way to do that is by copying the
Then once you launch WinDBG, add that path to your Symbol Path:
Each activity is broken up into Lessons and can be accessed by using the links on the upper right of the screen:
On newer versions, it will look a little prettier. I promise, i'll put in that new HeapSpray function soon :)
Feedback welcome!
I've been an adjunct professor at NYU Poly for almost two years now. It's been a great experience for a number of reasons, one of which is because I'm teaching a hot topic: Vulnerability Analysis and Exploitation. The course is the next iteration of the pentest.cryptocity.net content that evolved into the CTF Field Guide by Dan Guido, Trail of Bits, and a bunch of other industry professionals. It takes a student with some minor programming knowledge and submerges them into exploitation. When the student comes out, they have successfully exploited IE on Windows 7, bypassing DEP and ASLR. It's an awesome, but sometimes overwhelming experience for every student who takes it.
Each semester I start the class off with a survey to gauge the student's experience level: No surprise here, most have little to no experience when it comes to real-world exploitation on Windows. This results in a "revamping" period for the student where they have to work extra hard getting used to WinDBG and IDA.
I wanted to create something that would help ease the students into the learning environment, and that's what FSExploitMe is; a tutorial that walks you through the basics of WinDBG and general exploitation in a browser environment.
Installation
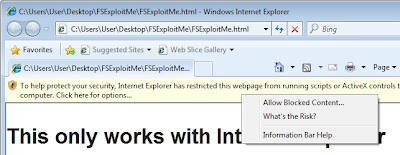
FSExploitMe is a self-contained, Active X based tutorial that you download and run locally within your browser. You'll want to run this in a VM, as it makes your browser vulnerable to attack. Ensure you have the Microsoft Visual C++ 2010 Redistributable Package installed. Then just double clickFSExploitMe.html to get started. You'll have the allow the extension to run by right clicking the banner and selecting "Allow Blocked Content...":Next Internet Explorer will ask you if you'd like to allow the active content to run, click "Yes":
Then finally you'll get a UAC prompt, click "Yes" here as well:
FSExploitMe should be all ready to go now:
Internet Explorer 8 looks a little less pretty then newer versions. IE8 is the recommended version strictly because Lesson 3 of FSExploitMe executes a HeapSpray that will not work on newer versions of IE. You can easily replace that function to use a newer HeapSpray, I just haven't done that and tested it on all other IE versions. That being said, future iterations of FSExploitMe will include a more robust HeapSpray Function.
It will help to have Symbols when you start debugging. The easiest way to do that is by copying the
FSExploitMe.pdb file to the C:\Windows\Downloaded Program Files directory.Then once you launch WinDBG, add that path to your Symbol Path:
.sympath+ C:\Windows\Downloaded Program Files
About the Lessons
When you first openFSExploitMe.html in your browser, you'll arrive at the welcome screen which gives you an overview of the Installation plus learning resources to get you off the ground with x86, IDA and WinDBG if you have absolutely no experience with them. You can return back to this page by clicking the "FSExploitMe" heading on the upper left of the page.Each activity is broken up into Lessons and can be accessed by using the links on the upper right of the screen:
On newer versions, it will look a little prettier. I promise, i'll put in that new HeapSpray function soon :)
Lesson 1 - Learning WinDBG
Lesson 1 is entirely dedicated to WinDBG since it is so important to the whole exploitation process. The questions will require you to set breakpoints, dig into memory, and execute some common commands to obtain answers.Lesson 2 - Stack-Based Overflow
Lesson 2 is focused around exploiting a basic stack-based overflow. The questions require you to understand how the stack operates, how to triage a stack-based overflow and finally how to exploit the condition. The first round walks you through the exploitation, the second is a bit harder - there is no walkthrough and it requires the use of IDA.Lesson 3 - Use-After-Free on the Heap
Lesson 3 walks you through a use-after-free vulnerability on the heap. The questions help you understand how data is stored on the heap, how virtual function tables and pointers are structured, how to triage a use-after-free and finally how to exploit it. This very much mimics a traditional browser use-after-free and should get you on the right track when you have to tackle a real-world vulnerability.Upcoming Lessons
The next few lessons that will be written will focus on bypassing exploit mitigations! Stay tuned!Download
FSExploitMe is available for download now! Answers can be provided if you just ask me for them, and you're not one of my students :)Feedback welcome!