By Deepak Choudhary.
Many application providers are considering implementing a more robust login mechanism to their applications as single layer authentication is no longer considered a secure approach. The trend is to add an additional authentication layer after main login surface. It could be anything like OTP based (text message), secondary authentication questions, voice calls etc...
It’s common for the application provider to setup a second layer on their end but there are also a few third party providers in the market. Google’s “Two factor authentication” is arguably the most popular and the subject of this blog post.
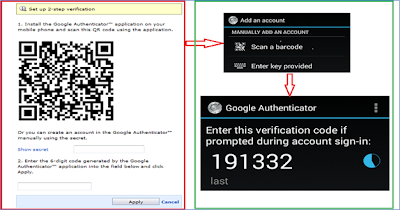
In order to leverage the Google Authenticator, the user needs to install the mobile application and then synch with application server. Once the user logs into the first page of the application, they will be presented with the Google Authentication verification prompt. The user can scan the on-screen QR code or manually enter a secret as shown below. Once the process is completed, the user can work without any connectivity.
The main difference in what the algorithms are fed is that the HMAC OTP uses a counter for input feed where the Time based OTP (TOTP) is seeding with the current time. For TOTP, the client and the server’s time must be in sync or the process will not complete. Network time protocol (NTP) is a key component to facilitate TOTP. In contract to TOTP, HMAC OTP uses a counter used instead of time. The counter increases on both sides once OTP is generated.
References:
Many application providers are considering implementing a more robust login mechanism to their applications as single layer authentication is no longer considered a secure approach. The trend is to add an additional authentication layer after main login surface. It could be anything like OTP based (text message), secondary authentication questions, voice calls etc...
It’s common for the application provider to setup a second layer on their end but there are also a few third party providers in the market. Google’s “Two factor authentication” is arguably the most popular and the subject of this blog post.
Overview
Google’s Two Factor Authenticator is the smartphone-based application that generates a one-time password used in secondary authentication. End users have option to enable this option within the setup on their smart phone.In order to leverage the Google Authenticator, the user needs to install the mobile application and then synch with application server. Once the user logs into the first page of the application, they will be presented with the Google Authentication verification prompt. The user can scan the on-screen QR code or manually enter a secret as shown below. Once the process is completed, the user can work without any connectivity.
OTP Generation
Google Authenticator uses two type of algorithm for generating OTPs. Both algorithms are supplied as follows:The main difference in what the algorithms are fed is that the HMAC OTP uses a counter for input feed where the Time based OTP (TOTP) is seeding with the current time. For TOTP, the client and the server’s time must be in sync or the process will not complete. Network time protocol (NTP) is a key component to facilitate TOTP. In contract to TOTP, HMAC OTP uses a counter used instead of time. The counter increases on both sides once OTP is generated.
Considerations
From a security prospective, OTP should take into consideration the same key elements as most other multifactor authentication mechanisms. For example:- Cross account OTP usage
- OTP expiration
- OTP reuse
- OTP length , etc
References: